
|
|
| Identity and Access Management |
Identity and access management is a cross-functional process that helps organizations to manage who has access to what information over a period of time. Poor or loosely controlled identity and access management processes may lead to organizational regulatory noncompliance and an inability to determine whether company data is being misused.
Sync Solutions Identity and Access Management solution utilizes CA digital certificate, digital envelope, encrypted signature and other asymmetric key encryption technologies to identify authorized users and ensure reliable, complete information transfer.
At the core of authentication system, authentication server intelligently manages remote user access to network and applications, and controls the entire AAA (authentication, authorization and accounting) process. Upon login, user is promoted to insert smart card. Authentication server reads remote user profile via encrypted tunnel and retrieves the matching authorization files.
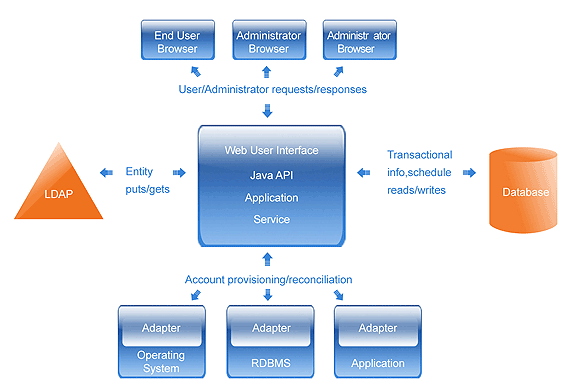
A typical identity and access management system has the following components:
Authentication service subsystem Provide server API, process user authentication request, recognize user identity and control user access to applications
Authentication management subsystem Manage user profile, query/modify/delete directory, deactivate user account and enable user access control
Authentication database Enable user mapping between smart card and account name
Secure Key (USB smart card) Store digital certificate and private key for encryption/decryption
 |
|
|
|



